| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
login
|
|
||||
|
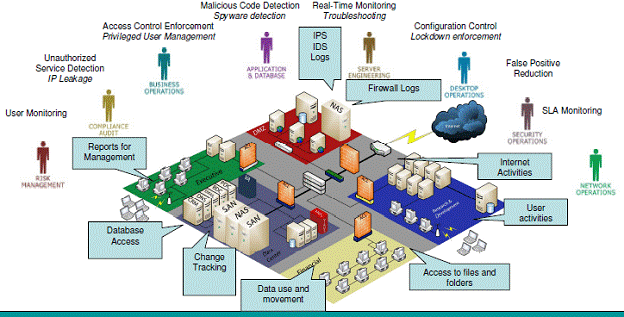
What is SIEM? Security Information and Event Management solutions are a combination of the formerly disparate product categories of SIM (security information management) and SEM (security event management). SIEM technology provides real-time analysis of security alerts generated by network hardware and applications. The objective: To help companies respond to attacks faster and organize mountains of log data. Security Information and Event Management (SIEM) technologies take part in a crucial role in addressing the compliance, efficiency, and security needs of an enterprise. The central part of SIEM technologies is the ability to collect security data from all the critical assets on a network and present that data as actionable information via a single interface. SIEM solutions come as software, appliances, or managed services. Increasingly, SIEM solutions are being used to log security data and generate reports for compliance purposes. SIEM intelligence added to networks (intelligent behavioral networks and not only signature based security). Identification of suspicious patterns of user behavior and hard to detect attacks. Monitoring and reporting of internal activities for compliance. Aggregation and correlation of logs along with storage of critical alerts. Vulnerability research and countermeasures. Secure communication between customer/MSSP and our Command and Control. 24/7 tech support from certified professionals. On-demand reports. SIEM Network Security will elevate threat visibility and decrease the signal-to-noise ratios for swift reporting and incident response. Gain full visibility into all activities that surround and touch your sensitive data. Our SIEM Managed Service solution performs high rate, operationally effective event correlation, enabling fast identification and prioritization of critical ‘real’ issues and facilitating a centrally integrated response environment. SIEM Network Security helps organizations put a stop to inside threats and provides solutions that streamline log management. This provides an immense array of benefits by allowing security and network teams to achieve a holistic comprehension of their assets' security status, prioritize security incidents, and show compliance with regulations much more efficiently than in the past.
SIEM “in-the-cloud” SIEM Network Security’s SIEM Managed Service allows organizations of all sizes to obtain the benefits of SIEM technologies, without experiencing the drawbacks (extreme high costs implementing in-house SIEM). SIEM Network Security’s SIEM service delivers event aggregation, correlation, and reporting "in-the-cloud," which requires no prolonged software implementations. The SIEM service can be completely functional in a matter of days, instantly presenting the enterprise with actionable information, a consolidated view of the security status of their critical assets, and on-demand reports via the secure web-based Enterprise Security Portal. With this information, security and network teams can respond faster to security incidents, while painlessly achieving compliance with many industry regulations by demonstrating control effectiveness.
Inside Threats Statistics indicate that 70 to 80 percent of cyber-attacks or breaches of security are either performed or occur on the inside. Support for Internal Source Devices: SIEM Managed Service is ideally suited for today’s compliance-oriented requirements, because it provides support for data collection and analysis from internal assets, such as operating systems, databases, and applications. By contrast, MSSPs typically do not support internal sources, due to design restrictions, and thus are limited to perimeter monitoring. One of our goals is to work side-by-side with MSSPs and in-house NOCs by adding key extra security layers to today’s vulnerable networks. You will see the SIEM technology's real-time response to policy violations, insider threats, network attacks, virus attacks, unauthorized application usage, inappropriate web browsing, and USB mass storage devices.
Defense-In-Depth Strategy A defense-in-depth strategy (industry best practice) utilizes multiple devices: Firewalls, IDS, AV, AAA, VPN, User Events - LDAP/NDS/NIS/X.500, Operating System Logs, which can effortlessly generate hundreds of thousands of events per day, in some cases, even millions. No matter how good a security engineer is, about 1,000 events per day is a practical maximum to deal with. If the security team is to remain small, it needs to be equipped with good SIEM services.
|
||